- Home
- Cyber Warfare – Iran, Demonstrations, Exploding Steel Plants and the Albanian Connection
12 October 2022
Cyber Warfare – Iran, Demonstrations, Exploding Steel Plants and the Albanian Connection
Hackers again hit Iranian state TV this weekend, posting an image of the Supreme Leader in rifle crosshairs. Who is behind the hacks and what is the Albanian connection in this latest round of an undeclared cyber-war?
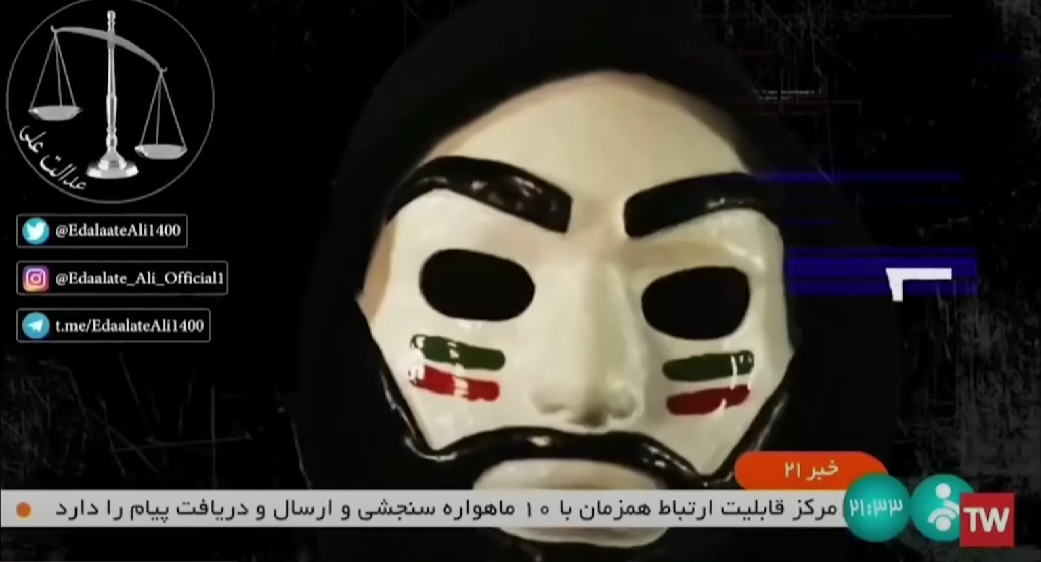
Image: Screen grab from Iranian state television broadcast
On Saturday, October 8, various channels of Iranian state TV were briefly hacked in an audacious new move that appears to support the widespread and still ongoing protests stemming from the death of Mahsa Amini. The hack started by momentarily showing a mask in vaguely ‘Anonymous’ fashion before switching to a screensaver photo of the country’s supreme leader Ayatollah Ali Khamenei caught in a sniper’s crosshairs while bathed in flames. A message in Farsi translated as “The blood of our youth is on your hands” was accompanied by photos of Mahsa Amini and three young victims of the heavy-handed government reaction to the demonstrators, a brutal response that is believed by now to have killed over 180 including at least 19 children.
Image: Screen grab from Iranian state television broadcast
The blame (or credit) for this latest attack was claimed by a group called Edalat-e Ali (Ali’s Justice), who had made a similar attack earlier in the year and, back in 2021, had hacked CCTV cameras in an Iranian prison to provide evidence of the abuse of inmates.
The general response of the Western media was one of barely suppressed crowing – hints of “you had it coming” that seem understandable given the awful clampdown that has been perpetrated. However, while not making any excuses for that brutality, the press seem to be overlooking an underlying theme of an undeclared cyber war on Iran - attacks over several years at the hands of a selection of enemies, some of them likely Western-backed proxies.
The Albanian Connection
Almost by definition, a group of hackers is likely to keep its identity secret, but the fact that Iran has been experiencing an almost constant barrage of cyber-attack gets little media attention. At least, not until it retaliates. A fascinating recent case was in July 2022 when a massive cyber blitz hit the national institutions of Albania, essentially knocking out almost all government functions in that country for a while. Though denied by the Islamic Republic, it was widely accepted that Iran orchestrated the attack. The White House officially pointed the finger at Tehran in September, and envisaged “further action to hold Iran accountable for actions that threaten the security of a U.S. ally.” This would include additional sanctions and severing diplomatic relations between Albania and Iran.[1]
As if to show disdain for such an announcement, another big cyber-attack, presumably Iranian, hit Albania’s police computer network a couple of days later, leading to queues at borders as arrivals and departures had to be handled manually.
But is Tehran crazy enough to play with Albania like a cat toying with a mouse, just for the fun of it? Or - to practice its capabilities? Dig a little deeper, and things look rather different.
The Curious Saga of MEK
Hidden away, at the end of just a few western articles on the Albania events, you might find a throwaway comment about “MEK.” That’s a radical dissident group who were due to be part of an anti-Iran meeting in Albania at the time of the July hacker attacks. MEK (Mujahadin-e Khalq, aka the People’s Mujahedin Organization of Iran) was described by CNN as “an Iranian group that advocates the overthrow of the Iranian government.” While that statement may be true, it glosses over some fairly major details. In the 1970s, the group had started as an anti-Shah outfit and was classified as a foreign terrorist organization by Washington and others for “the killing of U.S. citizens in Iran in the 1970s and an attack on U.S. soil in 1992.” However, MEK’s terrorist status was lifted in 2012 after the group, for decades based in Iraq, claimed to have renounced violence. Journalists suggested that intense lobbying from some sections of the US security apparatus had helped their cause and that the group’s leader Maryam Rajavi had “met with prominent US politicians such as Rudy Giuliani [and] John Bolton,” who are known for hawkish positions against Tehran. Informed commentators urged caution, describing MEK as having been “politically irrelevant in Iran since at least the mid-1980s.” At the same time, one anonymous US official was quoted as saying, “we have no confidence that the MEK is an organization that can promote [the] democratic values that we would like to see in Iran.”
PMOI followers demonstrate against the bombing of camp liberty in Iraq. Image: STRINGER Image/Shutterstock
MEK and Albania
OK, so what’s all this got to do with hacking in Albania? Well, part of the conundrum for the US was that 3400 MEK operatives were based at an Iraqi base called Camp Ashraf, from which Baghdad had long wanted the troublemakers ejected. For four years, until early 2016, America housed them at ‘Camp Liberty’ near Baghdad Airport while trying to figure out what to do with these folk who had previously been branded terrorists but might prove useful in Washington’s anti-Iran strategy.
Finally, the group was persuaded to decamp to – you guessed it – Albania, where, judging from Albanian news reports, they have proved rather difficult guests. Photos from a 2016 press conference in Tirana at which the then US Secretary of State John Kerry thanked Albania for accepting the rehoused MEK members, saw the Albanian Prime Minister looking decidedly uncomfortable at the prospect. It’s widely supposed that Tirana had been forced to accept the possibility as early as 2013. The deal was sweetened by a 20 million USD donation made through the UN, and once in place, MEK purchased an abandoned former university campus which it renamed Camp Ashraf 3. They created “a de facto enclave in Albania which is outside the law, just as they did in Iraq” and rekindled “the conditions of isolation and cultic control which have always prevailed for the membership.”[2]
From their new Albanian base, it appears highly likely that the MEK retrained as cyber warriors, adding to other efforts to destabilize Iran’s nuclear efforts. In November 2020, when veteran Iranian nuclear scientist Mohsen Fakhrizadeh was assassinated using a “remote-controlled machine gun… controlled by satellite," Tehran blamed MEK for the audacious, highly technical killing, suggesting that they might have worked in conjunction with the Israeli secret service agency Mossad. Albanian academic Olsi Jazexhi has described the hosting of MEK in Albania as “an American-Israeli affair” and evidence of American hegemony over Tirana. He also told the Tehran Times that the group was highly active in spreading anti-Iranian misinformation within the EU. In 2021 Facebook dismantled a veritable ‘troll farm’ of over 300 accounts aimed at spreading anti-Iranian propaganda. In this light, it is perhaps not surprising that Tehran would fight back against MEK’s reluctant Albanian hosts. Even if the exact source of this week’s Edalat-e Ali hack is unknown, it’s not the first time this year that they have struck. In previous attacks (January 27 and February 1), the hackers included not just anti-Khamenei slogans but also photographs of MEK leaders.
President-elect of the National Council of Resistance of Iran (NCRI) Maryam Rajavi, Vice President Mike Pence and Karen Pence visit the Resistance's expo, in Ashraf 3, home to thousands of members of the principal Iranian opposition movement, the Mujahedin-e Khalq (PMOI/MEK), Maryam Rajavi shows Mike Pence the pictures of the victims of the Iran massacre. Image: Siavosh Hosseini/SOPA Images/Sipa USA via Reuters
Other Cyber Attacks on Iran
Iran has been subjected to many other destructive hacker attacks. Less than two weeks before the first cyber strike against Albania in June, a group calling itself Gonjeshke Darande (Predatory Sparrow) attacked Khuzestan Steel, apparently causing a fire that crippled Iran’s second-biggest steel manufacturers for the foreseeable future. Attacks also hit the Mobarakeh and Hormozgan steel companies causing less damage. Predatory Sparrow had earlier paralyzed Iran’s domestic petrol distribution system in October 2021 and had hijacked computers and displays of the transport ministry and railway system in July 2021. A cyber analyst quoted by the BBC suggested that the sophistication of such attacks suggests that the hackers are likely to be “operated, or sponsored by, a nation-state.” The Khuzestan Steel incident was of particular interest to cyber-crime watchers as the hackers not only managed to capture CCTV footage to show off their work; they also made a statement saying that the attack had been “carried out carefully to protect innocent individuals.” Many speculated that the latter was less likely the sentiment of noble criminals than that of a state organization from which duty-of-care risk assessments might be required.
Possibly the most serious state-level cyber attack on Iran was the Stuxnet virus which, between 2007 and 2010, catastrophically infected around 2000 nuclear centrifuges causing years of delays in the Iranian Uranium enrichment programme. Widely assumed to have been spearheaded by the CIA and Mossad, Stuxnet is considered the first high-impact cyber weapon and the instigator of a worldwide cyber arms race. It has also gone on to infect computer systems around the globe.
Dangers Ahead
Returning to this week’s hack against Iranian TV, Edalat-e Ali’s messages of support for demonstrators against the harsh government crackdown chime well with global public opinion. However, it is always worth being aware of the broader context and the general dangers of any arms race – digital and physical. While we make no attempt to justify Iran’s reactions on the street, the background might give at least some credence to Tehran’s somewhat paranoiac sense of being attacked by a concerted coalition of anti-regime players. For most western commentators, the enemy of one’s enemy is near enough to one’s friend. But as we have seen with MEK[3], the waters of cyber warfare are largely untested, and their waves can be very turbulent.
[1] The timing of this announcement was quite interesting, Iranian media seeing a barrage of Iran-bashing as helping Biden to shunt out of touch any decisions to respond to the latest JCPOA sanctions proposals till at least after the Israeli legislative elections and US mid-terms in November.
[2] according to security consultant Massoud Khodabandeh on HuffPost. Khodabandeh was himself once a high ranking MEK member.
[3] Although likening the cyber-attacks to being bombed, Albania stopped short of invoking Article 5 that would have called for a NATO military response, avoiding a full scale international confrontation as well as much greater delving of public interest into the background of the issue.
Read this next






